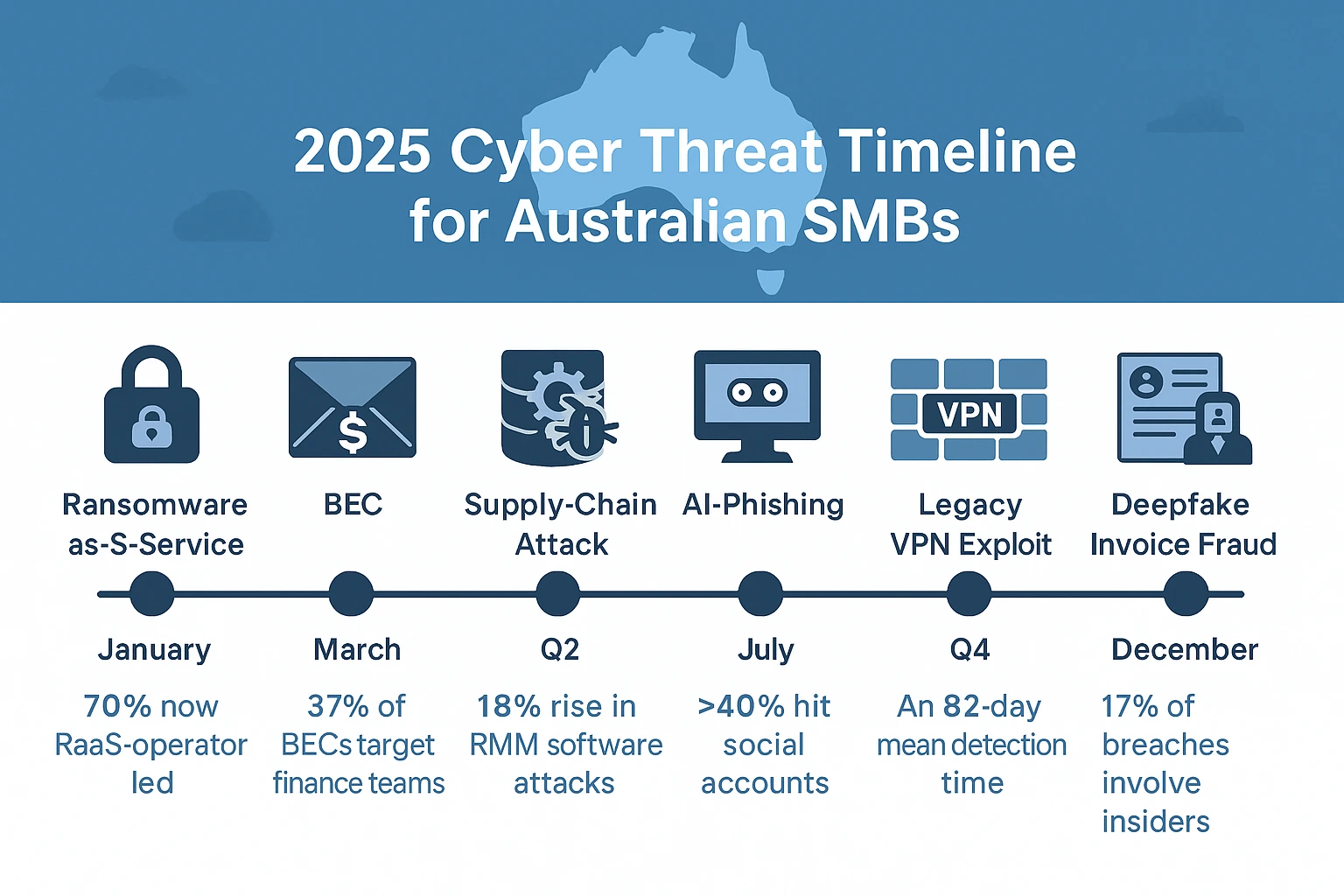
Australian small and mid-sized businesses faced 15 % more cyber incidents in FY 2024–25 than the year prior (ACSC Annual Report). Below is a data-led snapshot of the threats, sectors and controls that matter most in 2025—plus a free 30-page PDF for deeper analysis.
Executive Summary (Quick Stats)
- 38 % of Australian SMBs experienced at least one ransomware attempt.
- AUD 97 000 average cost per incident, up 12 % YoY (OAIC NDB data).
- 82 days average dwell time before detection—unchanged from 2024.
- RaaS groups now account for 70 % of encrypting attacks.
- One in three successful breaches began with a Business Email Compromise (BEC).

Top 7 Threat Trends to Watch in 2025
- Ransomware-as-a-Service (RaaS) Expansion – New affiliate models cut entry barriers; ACSC logged > 220 Australian victims in six months.
- BEC Aimed at Finance Teams – AI generates near-perfect invoice wording; median loss AUD 64 000.
- Supply-Chain Attacks via MSP Software – Remote monitoring tools abused to push malware, highlighting vendor due-diligence gaps.
- AI-Powered Phishing Lures – Voice-cloned execs request urgent payments; deepfake audio quality now fooling MFA voice verification.
- Legacy VPN Exploits – Unpatched SSL-VPNs remain in production; proof-of-concept exploits published within 24 hrs of CVE release.
- Insider Threats in Hybrid Workplaces – Off-boarded staff retain SaaS tokens; 17 % of breaches linked to disgruntled employees.
- Deep-Fake Invoice Fraud – High-fidelity PDF invoices bypass visual checks; machine-readable watermarks recommended.
Industry-Specific Risk Breakdown
Sector | % Incidents (FY 24-25) | Median Downtime | Common Entry Point |
Healthcare | 17 % | 5.4 days | Legacy VPN exploit |
Construction | 15 % | 2.7 days | BEC targeting accounts payable |
Professional Services | 13 % | 3.1 days | RaaS via phishing macro |
Sources: ACSC Annual Threat Report 2025; CrowdStrike AU SMB telemetry.
Essential Eight Alignment for 2025
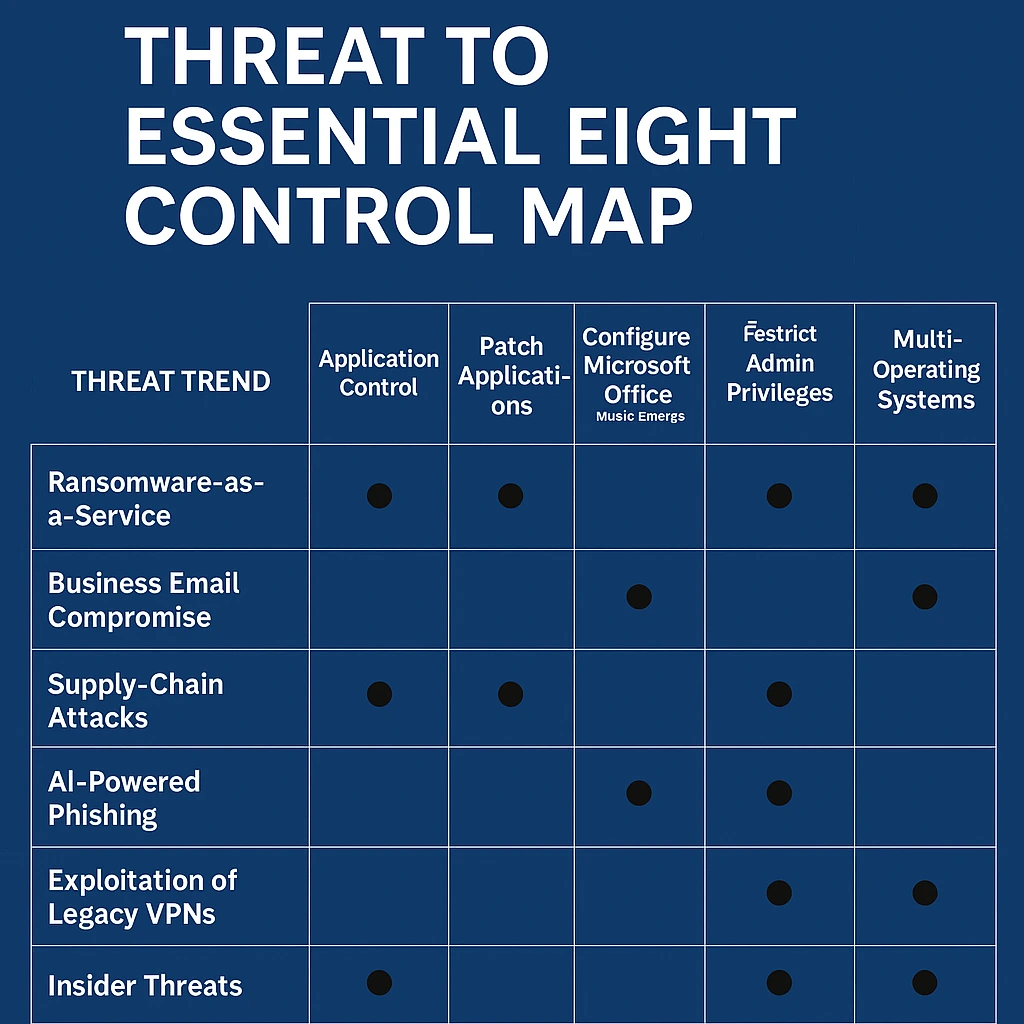
Threat Trend | Essential Eight Control | Quick Self-Check |
RaaS | Regular Back-ups | Offline copy older than 7 days? |
BEC | Multi-Factor Authentication | MFA on email & finance apps? |
Supply-chain attack | Application Control | Allow-list your RMM agents only? |
AI phishing | User Application Hardening | Block Office macros by default? |
VPN exploit | Patch Operating Systems | Firmware updates within 14 days? |
Insider threat | Restrict Admin Privileges | Deprovision leavers same day? |
Deep-fake invoice | Application Control + MFA | Segregate approvals over MFA? |
Need a deeper review? See our Essential Eight checklist or engage our cybersecurity services in Sydney team.
Mitigation Roadmap — 30 / 60 / 90 Days
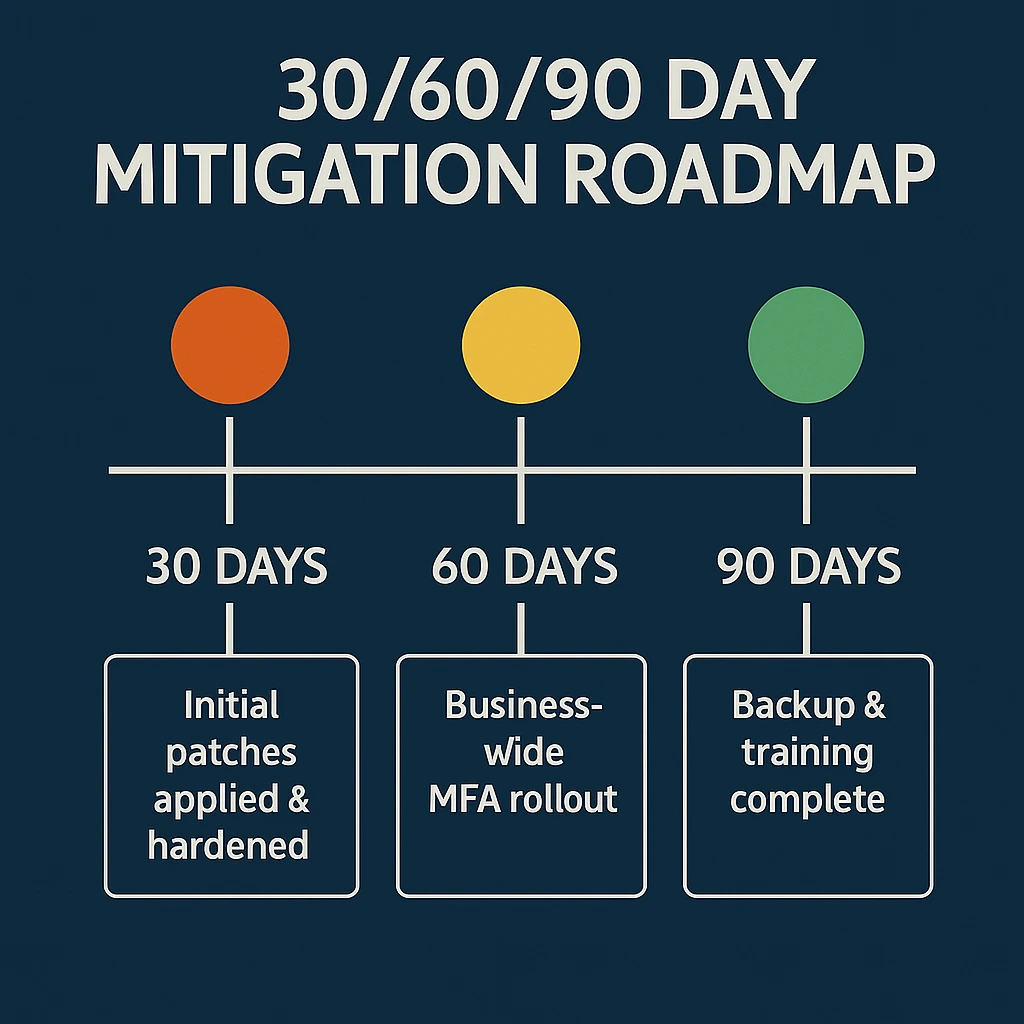
Timeline | Priority Actions |
Day 1–30 | Patch VPN firmware, enable company-wide MFA, audit back-up immutability. |
Day 31–60 | Deploy EDR across servers; run phishing-simulation training; review supplier access. |
Day 61–90 | Conduct tabletop ransomware drill; implement privileged access management (PAM); finalise incident-response playbook. |
Frequently Asked Questions
How does the 2025 threat landscape differ from 2024?
Ransomware dwell time is unchanged, but attack automation means incidents are 15 % more frequent for SMBs.
What is the average ransomware payout in Australia?
ACSC estimates the median ransom paid by SMBs in 2025 is AUD 54 000, although payments now void some cyber-insurance clauses.
Is cyber-insurance still paying out for SMBs?
Yes—but under stricter conditions. Insurers increasingly require Essential Eight Maturity Level 2 proof before honouring claims.