Cybersecurity threats are evolving, making Endpoint Detection and Response (EDR) a crucial tool for businesses. One of the key components of EDR is alerting, which helps security teams identify potential threats before they escalate. However, not all alerts are the same—there are Malware Alerts and Behavioral Alerts, and understanding the difference is critical to effective threat response.
At Code Hyper One, we help businesses filter out false positives, detect genuine threats, and respond effectively. Let’s explore the differences between Malware Alerts and Behavioral Alerts and how they contribute to a robust security strategy.
🔹 What Are Malware Alerts? 🦠
Malware Alerts are triggered when a file is identified as malicious based on its signature, reputation, or behavior. These alerts typically come from Antivirus (AV) tools or Threat Intelligence Feeds that compare files against known malware databases.
📌 Characteristics of Malware Alerts:
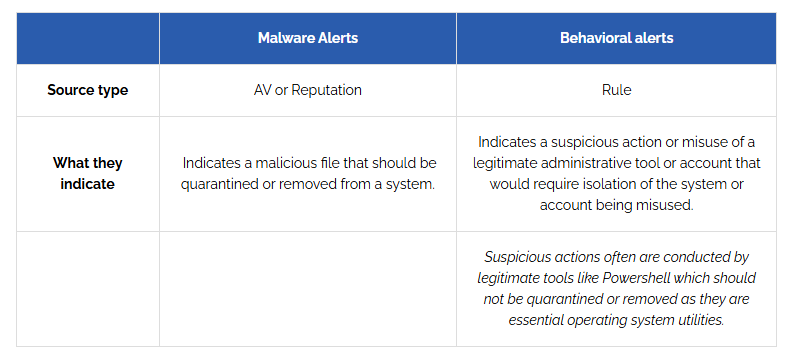
✅ Source Type: Antivirus (AV) or Threat Reputation Databases
✅ Detection Method: Compares files to known malware signatures
✅ Indicates: A malicious file should be quarantined or removed
✅ Common Examples:
- Trojan detected in an email attachment
- Ransomware file identified in a network share
- A backdoor installed via malicious software
🛡️ How to Respond to Malware Alerts:
🔹 Immediately quarantine or delete the file
🔹 Check logs to confirm where it originated
🔹 Scan all connected systems for similar threats
🔹 What Are Behavioral Alerts? 🚨
Behavioral Alerts are triggered when legitimate tools or accounts exhibit suspicious activity. Unlike Malware Alerts, these alerts don’t rely on known malware signatures; instead, they detect anomalies in system behavior.
📌 Characteristics of Behavioral Alerts:
✅ Source Type: Rule-based detection from EDR solutions
✅ Detection Method: Analyses user actions, process execution, and system activity
✅ Indicates: Potential misuse of a legitimate tool or account
✅ Common Examples:
- PowerShell running suspicious commands
- Administrator account logging in from an unknown location
- Unusual process execution in a critical system
📌 Important Note (from screenshot): Some alerts might flag legitimate system utilities like PowerShell, but these should not be quarantined or removed unless proven malicious.
🛡️ How to Respond to Behavioral Alerts:
🔹 Investigate first before taking action
🔹 Check user access logs and command execution history
🔹 Apply security policies to limit tool misuse
🔑 Malware Alerts vs Behavioral Alerts: A Quick Comparison
| Feature | Malware Alerts 🦠 | Behavioral Alerts 🚨 |
|---|---|---|
| Source Type | Antivirus (AV) or Reputation Database | Rule-based EDR Detection |
| Detection Method | Matches files against malware signatures | Analyses suspicious activity |
| Action Required | Quarantine or remove the file | Investigate before acting |
| False Positives? | Rare (if using up-to-date threat intelligence) | Common (legitimate tools like PowerShell may trigger alerts) |
| Common Threats | Viruses, Trojans, Ransomware, Rootkits | Account Takeovers, Misuse of Admin Tools, Lateral Movement |
🚨 Key Takeaway: Not all alerts require immediate deletion—some may be false positives that need further investigation!
🛡️ How Code Hyper One Can Help You Manage EDR Alerts
At Code Hyper One, we ensure businesses can accurately respond to security alerts without disrupting operations.
✅ EDR Implementation & Management – Deploying top-tier EDR solutions tailored to your needs
✅ Threat Intelligence & Monitoring – Filtering out false positives and detecting real threats
✅ Incident Response & Investigation – Ensuring effective and timely responses to security incidents
✅ Cybersecurity Awareness Training – Teaching teams how to handle alerts and reduce security risks
🚀 We help businesses filter the noise, detect genuine threats, and secure their digital assets.
🔎 Final Thoughts: Knowing the Difference Saves Time & Security Resources
🔹 Malware Alerts tell you what needs to be removed
🔹 Behavioral Alerts require investigation before action
🔹 Smart EDR management ensures security without unnecessary disruptions
At Code Hyper One, we help businesses detect, analyze, and respond to threats effectively—because cybersecurity is more than just quarantining files.
🚨 Need help managing EDR alerts? Contact Code Hyper One today to optimise your security response strategy!