The Role of Disaster Recovery in Cybersecurity

In today’s digital world, businesses face constant threats from cyberattacks, data breaches, and system failures. A single cyberattack can cripple operations, leak sensitive data, and cause financial loss. That’s why organisations must have a strong disaster recovery (DR) plan as part of their overall cybersecurity strategy. Disaster recovery plays a critical role in minimising damage […]
The Future of Cybersecurity: Integrating AI into Phishing Simulations

As cyber threats grow more sophisticated, businesses are increasingly focusing on improving their defense systems. One of the most common and dangerous threats is phishing, where attackers trick individuals into revealing sensitive information by posing as trustworthy sources. Phishing simulations have become a key tool in training employees to recognise phishing attempts, but now, a […]
Mastering Incident Response: A Step-by-Step Guide to Cybersecurity Resilience

Cyber threats are evolving at an alarming rate, making it critical for businesses to have a solid incident response plan in place. The NIST Cybersecurity Framework outlines a 4-step Incident Response Process that helps organisations detect, contain, and recover from cyberattacks efficiently. At Code Hyper One, we specialise in proactive cybersecurity solutions that help businesses […]
Malware Alerts vs Behavioral Alerts in EDR: Understanding the Difference
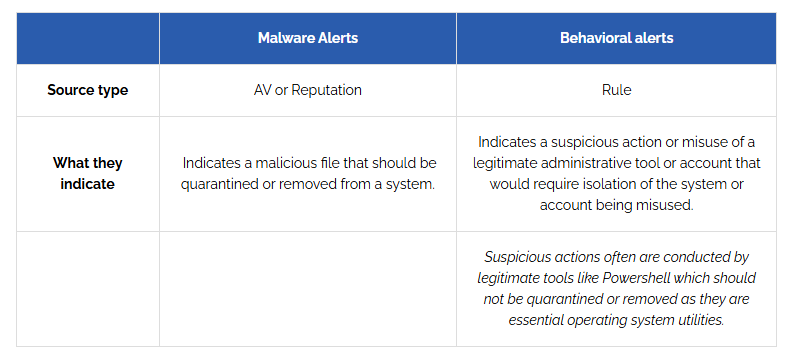
Cybersecurity threats are evolving, making Endpoint Detection and Response (EDR) a crucial tool for businesses. One of the key components of EDR is alerting, which helps security teams identify potential threats before they escalate. However, not all alerts are the same—there are Malware Alerts and Behavioral Alerts, and understanding the difference is critical to effective […]
Top Cloud Migration Benefits: Cost Savings and Flexibility

Cloud migration has become a game-changer for businesses worldwide. In fact, over 90% of organisations have already adopted some form of cloud technology to streamline operations, enhance security, and reduce costs. The cloud offers numerous benefits, including flexibility, scalability, and access to advanced technologies, making it an essential tool for companies aiming to stay competitive […]
Let Your Heart Be Stolen, But Not Your Precious Data! ❤️🔒

Love is in the air! 💕 Valentine’s Day is all about trust, connection, and deep bonds—just like the relationship you should have with your cybersecurity. While you’re busy planning the perfect romantic evening, cybercriminals are plotting their own kind of romance scams, phishing attacks, and data breaches. At Code Hyper One, we believe that while […]
What Is VoIP Technology? Learn How This Technology Transforms Calling

VoIP technology (Voice over Internet Protocol) is a system that allows voice calls to be made over the internet instead of traditional phone lines. It converts voice signals into digital data and transmits them online, enabling users to make calls from computers, smartphones, or VoIP-enabled devices. VoIP is widely used for its cost savings, flexibility, […]
How AI in Everyday Life is Quietly Reshaping Cybersecurity

Artificial Intelligence (AI) is no longer a futuristic concept—it’s part of our everyday lives. From voice assistants like Alexa and Siri to self-driving cars and personalized recommendations on Netflix and Spotify, AI is revolutionising how we interact with the world. However, as AI becomes more embedded in our daily routines, it brings along a host […]
What Is Email Security Gateway? How It Protects Your Business Inbox

An email security gateway is a tool that protects your inbox from unwanted or harmful emails. It works by filtering out spam, viruses, phishing attempts, and other malicious content before they reach your inbox. This helps ensure that your email communications remain safe and secure. Why is Email Security Important? Protects personal data: Keeps sensitive […]
9 Types of Vulnerability Scan Network to Protect Your System

Keeping your network safe from cyber threats is like locking the doors to your house. A vulnerability scan network helps you find weak spots in your system before hackers do. Think of it as a digital security check-up that keeps your data and devices protected. But did you know there are different types of vulnerability […]
Why Entra ID Protection is Key to Online Security

Importance of Entra ID Protection Entra ID Protection is critical for ensuring identity security and maintaining trust in the digital space. Here’s why it matters: Prevents Unauthorized Access: Blocks suspicious login attempts to protect sensitive accounts. Detects Security Threats: Identifies unusual activity to mitigate risks early. Secures Sensitive Data: Ensures personal and business information stays […]
Lessons from the PM Anthony Albanese Impersonating AI Scam

AI scams like the recent Hon Anthony Albanese impersonation remind us of the need for vigilance. Learn how to identify and protect yourself from AI-driven manipulation.
Why Do You Need a Smart Door Lock?

Installing a smart door lock is just one step toward stronger security at home—and your business needs a similar multi-layered approach. Learn why layered cybersecurity is essential for small businesses today.
Why RMM is important?

With an RMM solution, you can proactively monitor and maintain all your systems, ensuring security, efficiency, and scalability.
