Understanding Cloud Security Assessment
As more businesses move their infrastructure to the cloud, ensuring data security has become a critical priority. A cloud security assessment helps you identify vulnerabilities in your cloud environment, verify compliance, and strengthen your defences before attackers find gaps.
For Sydney-based organisations, regular security assessments are essential to maintain trust, meet compliance standards, and protect sensitive customer information.
Why Your Business Needs a Cloud Security Assessment
Cloud adoption brings flexibility, but it also introduces risks — from misconfigured storage to weak identity controls. A proper assessment:
- Detects potential breaches and misconfigurations
- Validates compliance with industry standards (ISO, NIST, ACSC)
- Strengthens cloud governance and user access controls
- Reduces downtime and data loss during incidents
If your business already relies on Microsoft Azure or Amazon Web Services (AWS), you can tailor assessments to those specific environments to uncover platform-level risks.
Key Areas Covered in a Cloud Security Assessment
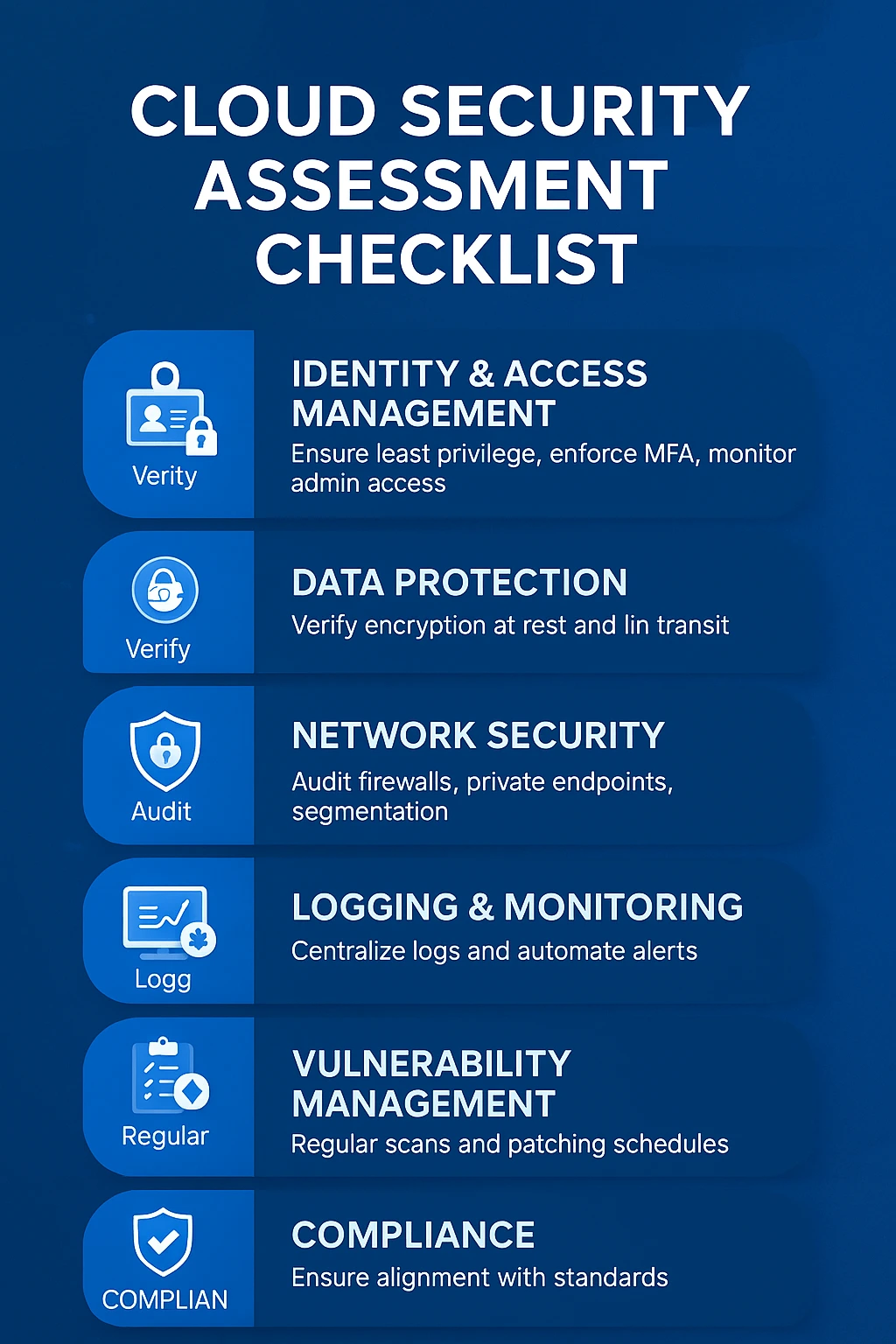
A robust cloud security assessment focuses on several critical components:
- Identity & Access Management – Ensure least privilege, enforce MFA, and monitor admin access.
- Data Protection – Verify encryption at rest and in transit.
- Network Security – Audit firewalls, private endpoints, and segmentation.
- Logging & Monitoring – Centralize logs and automate alerts.
- Vulnerability Management – Regular scans and patching schedules.
- Compliance – Ensure alignment with standards like ISO 27001 or ACSC guidelines.
AWS Cloud Security Assessment
An AWS cloud security assessment focuses on securing IAM policies, S3 buckets, CloudTrail logging, and GuardDuty monitoring. Reviewing these configurations ensures sensitive business data isn’t accidentally exposed through public access or over-permissioned roles.
Azure Cloud Security Assessment
In an Azure cloud security assessment, the emphasis is on Azure AD roles, Conditional Access policies, Key Vault usage, and network security groups (NSGs). Microsoft’s native tools like Defender for Cloud and Sentinel can enhance visibility and automate compliance monitoring.
Cloud Security Assessment Checklist
Here’s a concise checklist every business should review during an assessment:
- MFA enabled on all admin accounts
- Encrypted databases and storage
- Centralized logging (CloudTrail or Azure Monitor)
- Secure network configurations
- Updated patching policy
- Access review and role clean-up
- Backup and recovery validation
Following this checklist ensures your assessment isn’t just technical — it’s actionable.
Building a Reliable Cloud Security Framework
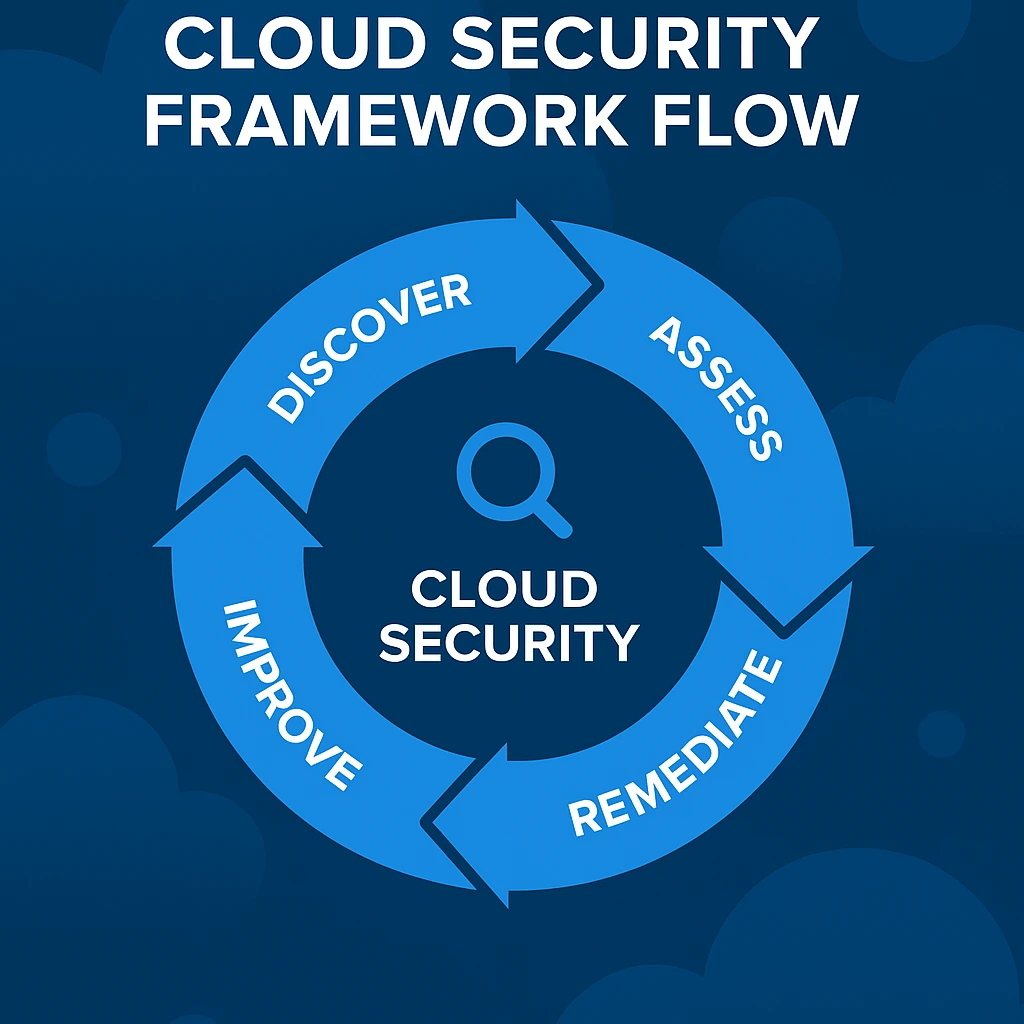
A clear cloud security assessment framework helps teams stay consistent and compliant. It includes:
- Defined asset inventory
- Continuous monitoring policies
- Automated compliance alerts
- Regular vulnerability scans
- Incident response playbooks
Businesses that adopt such frameworks reduce human error and improve long-term security posture.
Integrating Assessments with Continuous Monitoring
Completing a one-time audit isn’t enough. To maintain strong protection, integrate assessments with Security Operations Center (SOC) monitoring.
Your SOC services can detect threats 24/7 and respond faster to suspicious activities identified during assessments.
For ongoing improvements and system reviews, your IT consulting team can help design cloud governance policies and security automation.
Common Mistakes Businesses Make
- Treating assessments as one-time exercises
- Ignoring multi-cloud visibility gaps
- Not tracking remediation progress
- Skipping user training and phishing simulations
Avoiding these mistakes keeps your cloud environment resilient and your compliance posture strong.
Conclusion
A cloud security assessment isn’t just about technical audits — it’s about trust, compliance, and business continuity. Regular assessments empower Sydney organisations to safeguard their digital assets, reduce downtime, and stay ahead of evolving threats.
Frequently Asked Questions
1. What is a cloud security assessment?
It’s a detailed review of your cloud infrastructure that identifies security gaps, validates configurations, and ensures compliance with best practices.
2. How often should I conduct a cloud security assessment?
Ideally, every 6–12 months, or after major cloud changes like migrations, new integrations, or policy updates.
3. What’s the difference between AWS and Azure cloud assessments?
AWS assessments focus on IAM roles, S3 configurations, and logging. Azure assessments evaluate AD roles, Conditional Access, and Key Vault protection.






