Australian businesses lost over AUD 98 million to cyber incidents in 2024 alone (ACSC Annual Report). The Australian Signals Directorate (ASD) still recommends the Essential Eight as the minimum cyber-mitigation baseline for every organisation connecting to Australian Government networks or doing business with public agencies.
This guide gives you a plain-English, 2025-ready Essential Eight checklist—plus a downloadable Google Sheet to score your own maturity. Use it to brief the board, prioritise projects, and make a compelling case for budget.
Why the Essential Eight Matters in 2025
The quick version: unpatched systems and weak identities keep Australian SMBs on the radar of ransomware crews.
- ASD mandate: Commonwealth entities must reach Essential Eight compliance under the Protective Security Policy Framework (PSPF).
- Insurance leverage: Cyber insurers increasingly ask for proof of Maturity Level 2 before issuing or renewing cover.
- Supply-chain clauses: State government contracts—and many large primes—now reference the Essential Eight in vendor agreements.
Reference: ACSC Essential Eight Maturity Model PDF and PSPF 2023-25 Roadmap
Fail to comply, and you may face higher premiums, contract exclusion, or expensive breach notifications under the Privacy Act.
The 8 Essential Controls Explained
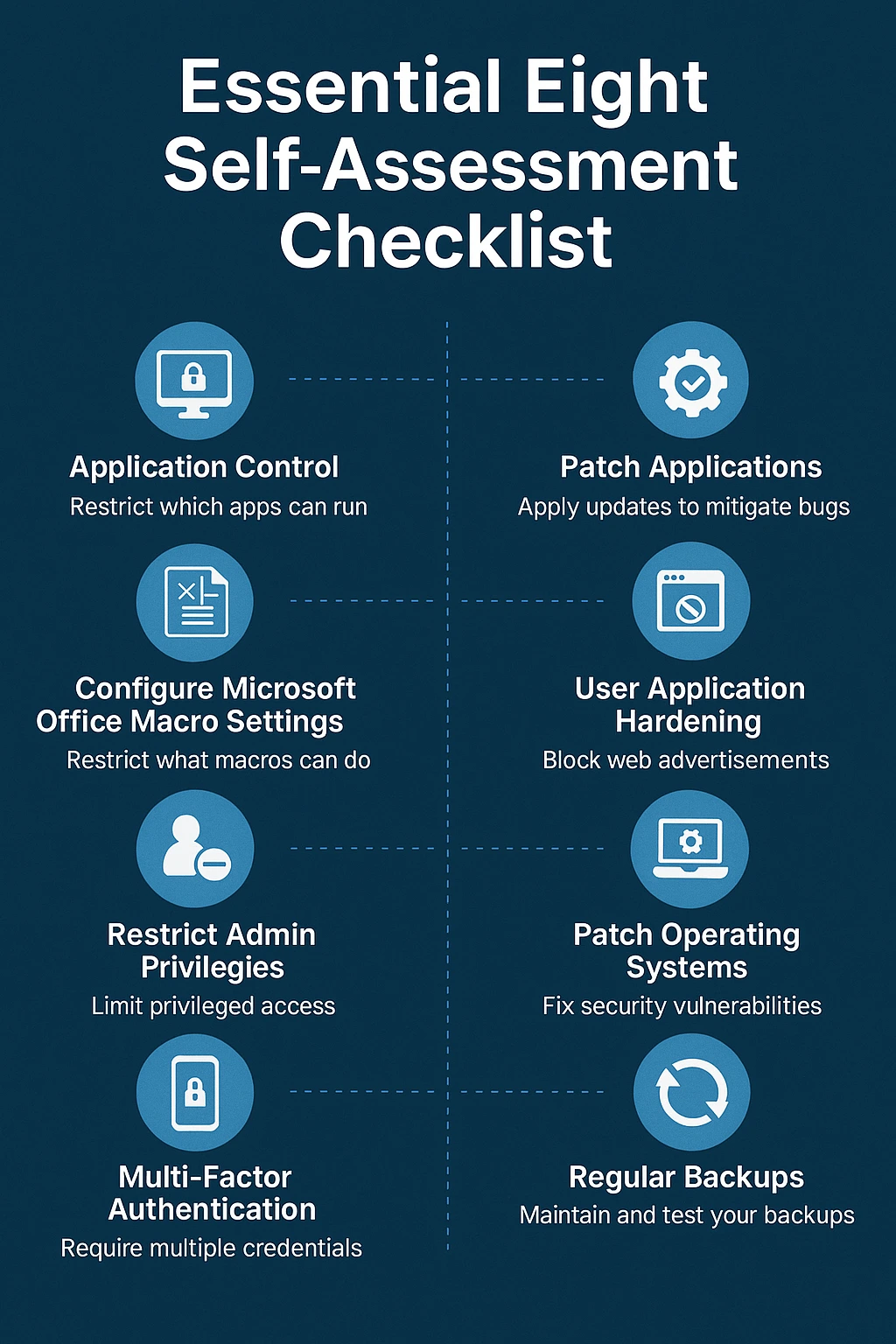
# | Control | Goal (plain English) | Key Tasks |
1 | Application Control | Stop unauthorised code | Allow-list approved apps; block unsigned scripts |
2 | Patch Applications | Close known exploits | Apply critical/high patches ≤ 14 days |
3 | Microsoft Office Macro Settings | Kill malicious macros | Disable internet macros; allow signed only |
4 | User Application Hardening | Harden browsers & apps | Remove risky plug-ins; disable Flash/Java |
5 | Restrict Administrative Privileges | Minimise “keys to the kingdom” | Separate admin accounts; review access 90-day |
6 | Patch Operating Systems | Seal OS holes | Deploy OS patches ≤ 14 days; reboot fleet |
7 | Multi-Factor Authentication (MFA) | Stop credential theft | Enforce MFA for VPN, email, SaaS |
8 | Regular Back-ups | Recover fast when hit | Daily encrypted back-ups; offline copy; quarterly restore test |
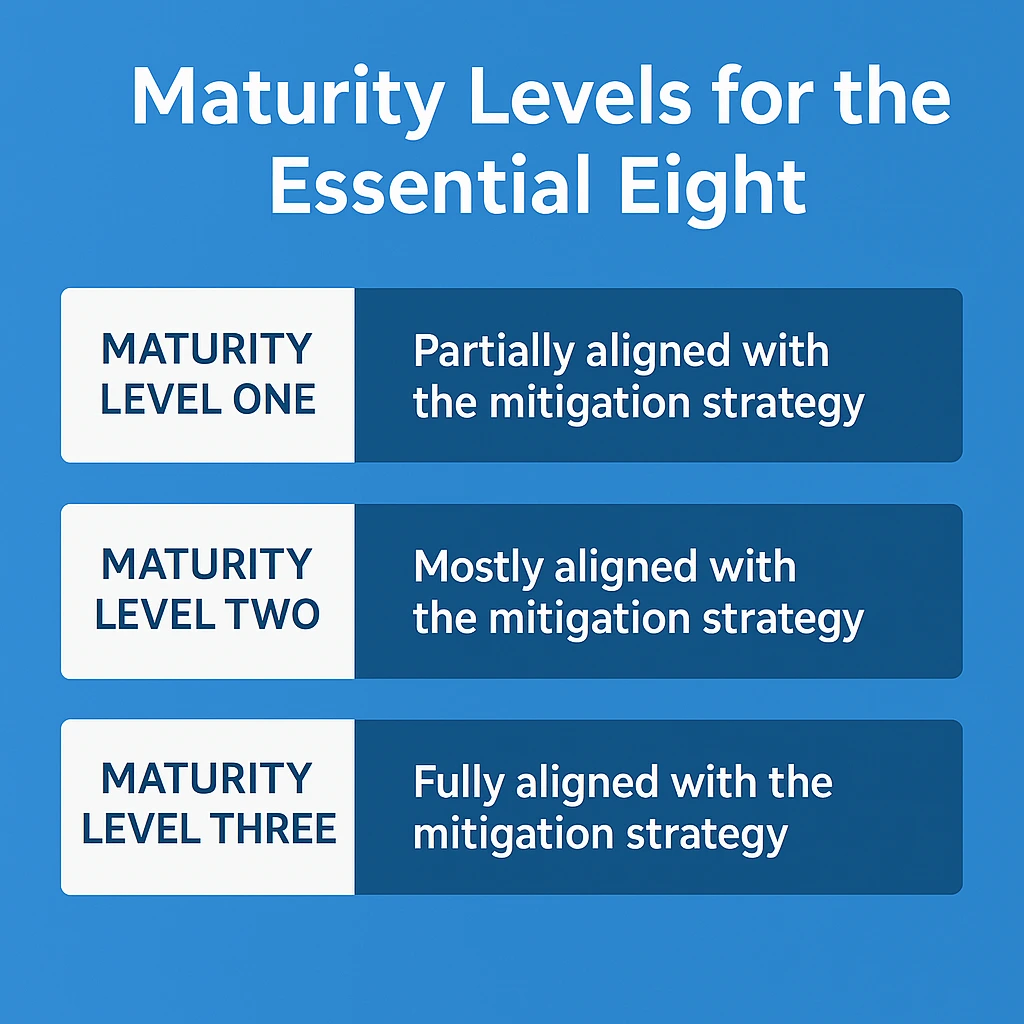
Call-out: Maturity Snapshot
Maturity Level 1 – Most controls drafted but ad-hoc; evidence inconsistent
Maturity Level 2 – Controls repeatable and monitored (minimum for insurers)
Maturity Level 3 – Proactive; controls integrated with SOC & automation
How to Use This Self-Assessment Checklist
- Download the Google Sheet checklist ▼ (free for Australian organisations).
- For each control, tick the tasks you’ve completed and paste evidence links (policy doc, Intune screen-shot).
- The sheet auto-scores your Maturity Level and highlights gaps in red.
- Export the summary tab to brief executives or external auditors.
Eligibility: The template is free for Australian-registered businesses and NFPs with ≤ 500 staff.
The Maturity Model (Levels 1–3)
Control | Level 1 | Level 2 | Level 3 |
Application Control | Basic allow-list | Hash-based allow-list | All executables + DLLs enforced; change management |
Patch Apps | Patches within 30 days | Critical patches ≤ 14 days | Virtual patching or WAF for zero-days |
Macro Settings | Disable in email | Block unsigned macros | Allow signed macros only; audit logs |
User App Hardening | Remove Flash/Java | Block ads & trackers | Content Security Policy enforced |
Admin Privileges | Named admin accounts | Privilege reviews 90-day | Jump boxes + Just-in-Time privileges |
Patch OS | Critical ≤ 30 days | Critical ≤ 14 days | Firmware & driver patch automation |
MFA | Remote users only | All privileged & remote | Phishing-resistant (FIDO2, Passkeys) |
Back-ups | Daily | Offline copy; test restore | Immutable storage; continuous replication |
What does “Level 3 compliance” mean?
In practice, Level 3 shows you can withstand a “sophisticated adversary”. Controls are automated, monitored, and continually improved—think SIEM alerts, immutable back-ups, and FIDO2 tokens across the board.
FAQs About the Essential Eight
Is the Essential Eight mandatory?
The Essential Eight is mandatory for federal agencies under the PSPF and strongly recommended for all other Australian organisations. Private firms adopting it enjoy lower cyber-insurance premiums.
What are the 8 essentials?
They are the eight mitigation strategies listed above—application control, patching, macro settings, user hardening, admin restriction, OS patching, MFA, and back-ups.
How do I meet maturity level 3?
Start by closing Level 1–2 gaps, then invest in automation (Intune, Defender, SIEM), immutable storage, and phishing-resistant MFA. Our Cybersecurity Services team can run a readiness audit.
Who enforces ASD compliance?
The Australian Signals Directorate (ASD) and your relevant portfolio Department oversee government agencies. In the private sector, enforcement is contractual (insurance, supply-chain) rather than regulatory.
What happens if I’m not compliant?
You risk higher premiums, loss of tenders, and greater breach impact—plus potential penalties under the Privacy Act if personal data is compromised.







