Vulnerability Scanning Services Sydney Australia
Protect Your Network with Comprehensive Vulnerability Scanning Sydney.
Contact us to learn more about how Code Hyper One’s vulnerability scanning services in Sydney, Australia can help protect your business from cyber threats.
Vulnerability Scanning Sydney AU by Code Hyper One
Vulnerability assessment services in Sydney is essential for safeguarding your business against the ever-evolving landscape of cyber threats. At Code Hyper One, our vulnerability scanning service provides automated detection of weaknesses in your network infrastructure, ensuring proactive identification and remediation of risks before they can be exploited by malicious actors.
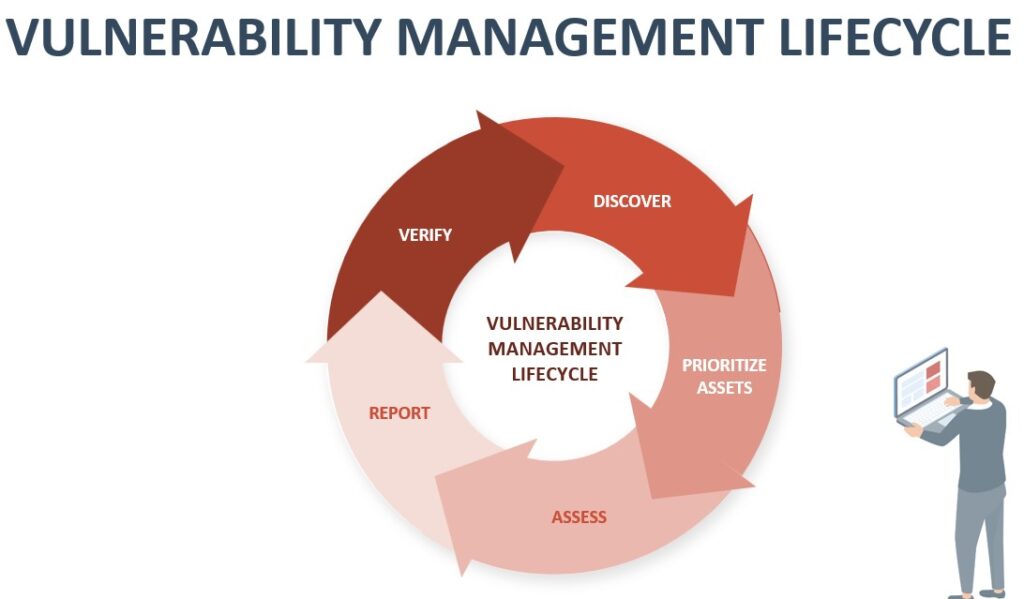
Internal & External Scans
Internal scans focus on threats, while external scans detect vulnerabilities.
Remediation Recommendations
Improve your defenses, and fortify your systems against future threats.
Compliance & Risk Management
Ensuring your organisation stays compliant with industry regulations.
Internal & External Scans
We conduct both internal and external vulnerability scans to identify risks across your network. Internal scans focus on identifying threats inside your network, while external scans target vulnerabilities in systems exposed to the internet.

Why Choose Code Hyper One for Sydney's Vulnerability Scanning Service?
At Code Hyper One, we provide a cost-effective and reliable way to continuously monitor and strengthen your network’s security. Our automated scanning solutions, combined with detailed, actionable reports, empower your team to stay ahead of potential vulnerabilities and maintain a secure environment for your business.
Secure Your Network Today
Contact us to learn more about how Code Hyper One’s vulnerability scan services in Sydney Australia can help protect your organization from potential cyber threats.
Microsoft 365 Services
Let us be your all-in-one IT partner and experience the peace of mind that comes with knowing your technology is in safe hands.

Purview Compliance
We make sure your organsation meets the ever-evolving regulatory standards and data governance requirements.

Endpoint Manager
We offer comprehensive services tailored to Microsoft Endpoint, ensuring enhanced security.

Exchange
We specialise in providing seamless email communication, robust security. and efficient management.

SharePoint
We provide seamless collaboration, content management, and workflow automation.

Teams
Tailored services for Teams, enabling seamless collaboration, communication, and productivity enhancements.
Code Hyper One Partners
By working with the best in the industry, we ensure that our clients benefit from the latest advancements and robust technologies to support their growth and success.











Code Hyper One Blog
Your go-to resource for the latest insights, tips, and trends in the world of IT.